Interview Questions
See the .NET folder for .NET questions and CompSci folder for general Computer Science/Theory questions
Lists (no sort - C#/.NET mixed):
Note: These questions have even less grouping than the C# questions... some of them ask about ancient things like SOAP and WinForms, lol
.NET Questions
Main components of .NET framework
.NET framework consists of 2 main components. They are:
- CLR- It is an execution engine that runs the code and provides services that make the development process easier.
- Framework Class Library- It has pre-defined methods and properties to implement common and complex functions that can be used by .NET applications.
How does the .NET framework work?
- .NET framework-based applications that are written in supportive languages like C#, F#, or Visual basic are compiled to Common Intermediate Language (CIL).
- Compiled code is stored in the form of an assembly file that has a .dll or .exe file extension.
- When the .NET application runs, Common Language Runtime (CLR) takes the assembly file and converts the CIL into machine code with the help of the Just In Time(JIT) compiler.
Now, this machine code can execute on the specific architecture of the computer it is running on.
Once you produce IL from your high-level code, you will most likely want to run it. This is where the CLR takes over and starts the process of Just-In-Time compiling, or JIT-ing your code from IL to machine code that can actually be run on a CPU. In this way, the CLR knows exactly what your code is doing and can effectively manage it.
Differentiate between Task and Thread (in .NET)
The thread represents an actual OS-level thread, with its own stack and kernel resources, and allows the highest degree of control. You can choose to Abort() or Suspend() or Resume() a thread, and set thread-level properties, like the stack size, apartment state, or culture.
While a Task class from the Task Parallel Library is executed by a TaskScheduler to return a result and allows you to find out when it finishes.
How does Garbage Collection work?
The Garbage collector frees the unused objects in memory.
The memory heap is partitioned into 3 generations:
- Generation 0: It holds short-lived objects.
- Generation 1: It stores medium-lived objects.
- Generation 2: This is for long-lived objects.
Collection of garbage refers to checking for objects in the generations of the managed heap that are no longer being used by the application. It also performs the necessary operations to reclaim their memory. The garbage collector must perform a collection in order to free some memory space.
During the garbage collection process:
- The list of live objects is recognized.
- References are updated for the compacted objects.
- The memory space occupied by dead objects is recollected. The remaining objects are moved to an older segment.
System.GC.Collect() method is used to perform garbage collection in .NET
Order of the events in a page life cycle
There are eight events as given below that take place in an order to successfully render a page:
- Page_PreInit
- Page_Init
- Page_InitComplete
- Page_PreLoad
- Page_Load
- Page_LoadComplete
- Page_PreRender
- Render
How do you apply themes to an ASP.NET application?
By modifying the following code in the web.config file, we can apply themes to ASP.NET applications:
<configuration>
<system.web>
<pages theme="windows"/>
</system.web>
</configuration>
.NET Web Forms vs ASP.NET MVC
Traditionally, the .NET Framework has been based on Web Forms. This was essentially an effort to create web services using Microsoft’s existing Visual Studio Tools without forcing developers to learn new scripting languages. Web Forms still allows developers to create quick and simple applications, and some legacy systems may still run as Web Forms.
ASP.NET MVC is increasingly the standard for contemporary developers, however. In a .NET interview, a strong candidate should be able to highlight the advantages of the Model-View-Controller (MVC) architectural pattern. MVC’s most important feature is that it allows applications to be broken down into discrete models, views and controllers, making them much easier to test during development.
Different types of cookies available in ASP.NET?
Two types of cookies are available in ASP.NET. They are:
Session Cookie: It resides on the client machine for a single session and is valid until the user logs out. Persistent Cookie: It resides on the user machine for a period specified for its expiry. It may be an hour, a day, a month, etc.
Security controls available on ASP.NET
Following are the five security controls available on ASP.NET:
<asp:Login> Provides a login capability that enables the users to enter their credentials with ID and password fields.
<asp:LoginName> Used to display the user name who has logged-in.
<asp:LoginView> Provides a variety of views depending on the template that has been selected.
<asp:LoginStatus> Used to check whether the user is authenticated or not.
<asp:PasswordRecovery> Sends an email to a user while resetting the password.
What is Encapsulation?
Another way of understanding encapsulation is to think of it as “hiding” the state of an object as private or protected.
Under this principle of information hiding, the internal workings of an object are segregated from the rest of the application.
This is useful because it makes it less likely that other objects can modify the state or behavior of the object in question.
What are MIME Types?
MIME stands for Multipurpose Internet Mail Extensions. It is the extension of the e-mail protocol which lets users use the protocol to exchange files over emails easily.
Servers insert the MIME header at the beginning of the web transmission to denote that it is a MIME transaction.
Then the clients use this header to select an appropriate ‘player’ for the type of data that the header indicates. Some of these players are built into the web browser.
What is the appSettings section in the web.config file?
We can use the appSettings block in the web.config file, if we want to set the user-defined values for the whole application. Example code given below will make use of ConnectionString for the database connection throughout the project:
<configuration>
<appSettings>
<add key="ConnectionString" value="server=local; pwd=password; database=default" />
</appSettings>
</configuration>
dataset.clone vs. dataset.copy
Dataset.clone copies only the structure of the DataSet which includes all DataTable schemas, relations, and constraints but it does not copy any data.
Dataset.copy is a deep copy of the DataSet that duplicates both its structure and data.
Events vs Delegates
Events notify other classes and objects when the desired action occurs in a class or object. A delegate is a type-safe function pointer that defines a method signature in CLI.
Managed vs Unmanaged Code
| Managed Code | Unmanaged Code |
|---|---|
| It is managed by CLR. | It is not managed by CLR. |
| .NET framework is a must for execution. | Does not require a .NET framework for the execution. |
| Memory management is done through garbage collection. | Runtime environment takes care of memory management. |
Code written in unsupported languages, such as Java, will produce unmanaged code, meaning developers can’t rely on the CLR to provide this kind of portability. Managed and unmanaged code are interoperable. Examples of unmanaged code used in .NET include COM components, ActiveX interfaces and Win32 API functions.
Pooling
Object Pooling is a concept for optimal use of limited resources through software constructs. The ready-to-use objects, connections, and threads are stored in a pool (group) of objects in memory for later use. For creating a new object, it is pulled from the pool and allocated for the request. Pooling helps in improving performance and facilitates scalability.
Connection Pooling There are 4 parameters that control the connection pooling behaviors. They are:
- Connect Timeout
- Min Pool Size
- Max Pool Size
- Pooling
What is a PE file?
PE stands for Portable Executable. It is a derivative of the Microsoft Common Object File Format (COFF). Windows executable. EXE or DLL files follow the PE file format.
It consists of four parts:
- PE/COFF headers- Contains information regarding. EXE or DLL file.
- CLR header- Contains information about CLR & memory management.
- CLR data- Contains metadata of DDLs and MSIL code generated by compilers.
- Native image section- Contains sections like .data, .rdata, .rsrc, .text etc.
Global Assembly Cache (GAC)
The Global Assembly Cache is a machine-wide code cache that is stored in a folder in the Windows directory. It stores the .NET assemblies that are specifically designated to be shared by all applications executed on the system
MEF
MEF stands for Managed Extensibility Framework. It is a library that allows the host application to consume external extensions without any configuration requirement.
Role-based Security
Role-based security is used to implement security measures in .NET, based on the roles assigned to the users in the organization. In the organization, authorization of users is done based on their roles.
For example, windows have role-based access like administrators, users, and guests.
Explain the different parts of an Assembly.
- Manifest – It holds the information about the version of an assembly. It is also known as assembly metadata.
- Type Metadata – It consists of binary information of the program.
- MSIL – Microsoft Intermediate Language code.
- Resources – List of related files.
What are MDI and SDI?
MDI (Multiple Document Interface): An MDI allows you to open multiple windows, it will have one parent window and as many child windows. The components are shared from the parent window like toolbar, menubar, etc.
SDI (Single Document Interface): SDI opens each document in a separate window. Each window has its own components like a toolbar, menubar, etc. Therefore it is not constrained to the parent window.
Stack vs Heap
Stack: Stack is a stored-value type that keeps track of each executing thread and its location. It is used for static memory allocation. Heap: Heap is a stored reference type that keeps track of the more precise objects or data. It is used for dynamic memory allocation.
Code Access Security
Code Access Security(CAS) is necessary to prevent unauthorized access to programs and resources in the runtime. It is designed to solve the issues faced when obtaining code from external sources, which may contain bugs and vulnerabilities that make the user’s system vulnerable.
CAS gives limited access to code to perform only certain operations instead of providing all at a given point in time. CAS constructs a part of the native .NET security architecture.
What is the use of manifest in the .NET framework?
Manifest stores the metadata of the assembly. It contains metadata which is required for many things as given below:
- Assembly version information.
- Scope checking of the assembly.
- Reference validation to classes.
- Security identification.
ADO.NET vs Entity Framework
ADO.NET provides better performance as it is directly connected to the data source, which makes the processing faster than Entity Framework as it translates LINQ queries to SQL first then process the query.
Entity Framework for CRUD operations ADO.NET for more control over the SQL sent to the DB
Transient, Scoped, Singleton
Transient objects are always different; a new instance is provided to every controller and every service.
Scoped objects are the same within a request, but different across different requests.
Singleton objects are the same for every object and every request.
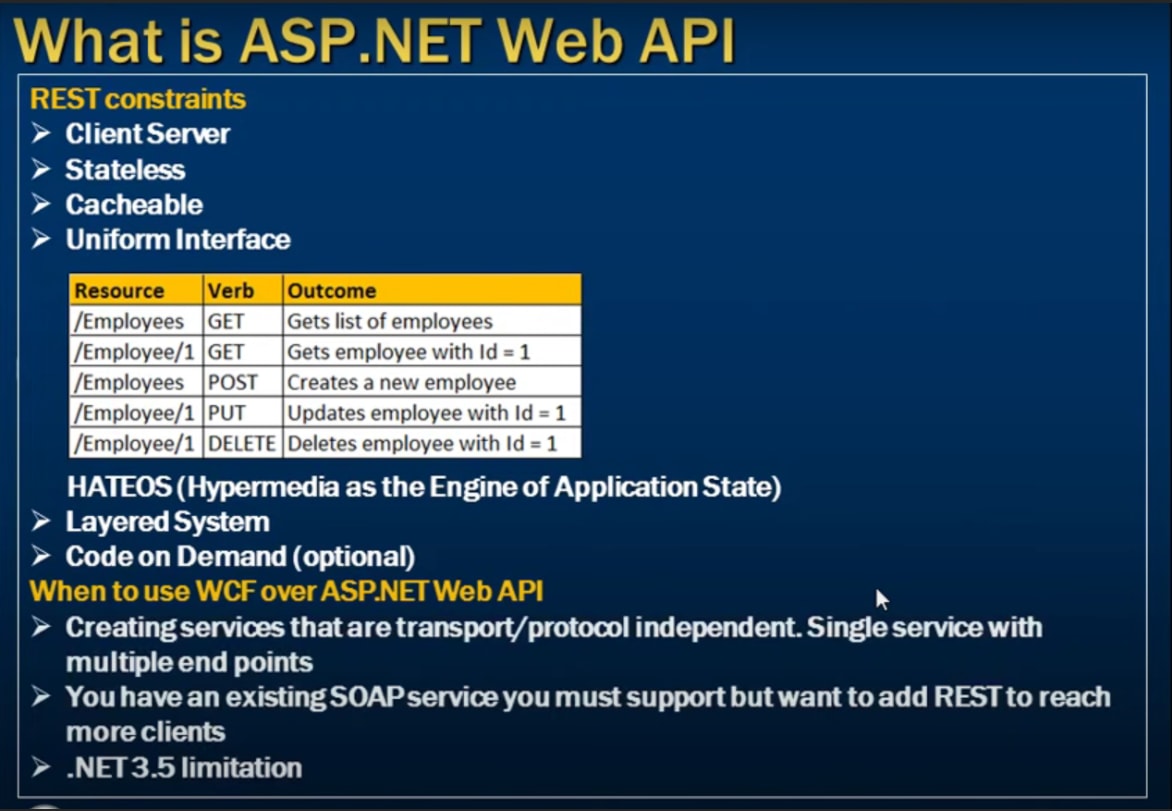
WCF vs Web API
In .NET there are multiple options for creating restful services:
- WCF (Windows Communication Foundation)
- Requires more config to create RESTful service
- WebAPI